前言
之前工作中很多初次接触密码学的小伙伴都会纠结于公钥,私钥,证书和签名分别是啥,怎么使用的,这里以golang为范例对这块的相关涉及到的内容进行一定的整理。
概念
- 私钥
- 只有自己知道的密钥叫私钥,能解开对应公钥加密的数据
- 公钥
- 公开的密钥叫公钥,能解开对应私钥加密的数据
- 证书
- 证书中心使用自己的私钥对需要颁布证书的公钥和相关信息一起加密,生成了证书,通过证书可以确定自己的公钥是否是正确的公钥。
- 签名
- 将内容生成摘要hash后对这个摘要hash进行加密,这个就是签名,能够通过解开签名和对内容进行hash进行匹配确定内容是否被修改过。
例子
接下来我们就开始在golang中开始玩起来
生成公钥/私钥
1 |
|
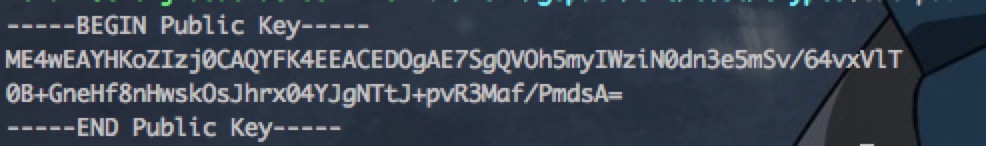
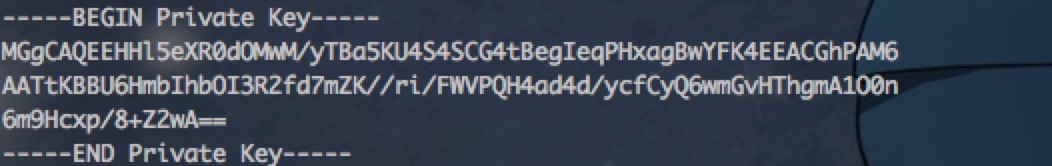
这里我们选用的是椭圆加密算法ECC生成的公/私钥对,并且将其输出到了文件,如下图所示
公钥
私钥
公/私钥加密与解密
在golang中对ECC只默认实现了签名算法(ecdsa),因此这里我们很遗憾要使用rsa进行加密与解密
1 | package main |
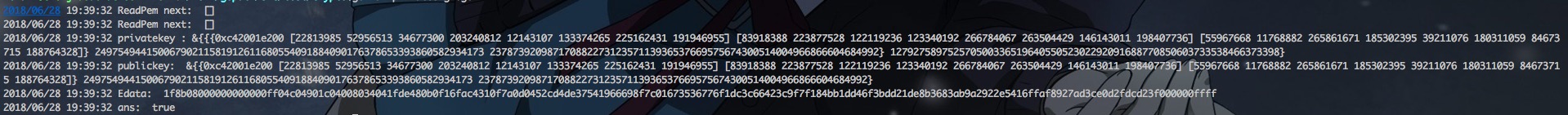
输出结果如下图所示:

可以看到加密后各种乱码,解密后完全正常
签名与签名校验
1 | package main |
这里我们可以看到,我们从之前的pem文件中得到了公钥和私钥,对一个字符串使用了md5摘要,然后对此进行了签名,得到了Edata,最后再根据公钥和md5摘要对这个签名进行了校验,得到了正确的答案
生成证书
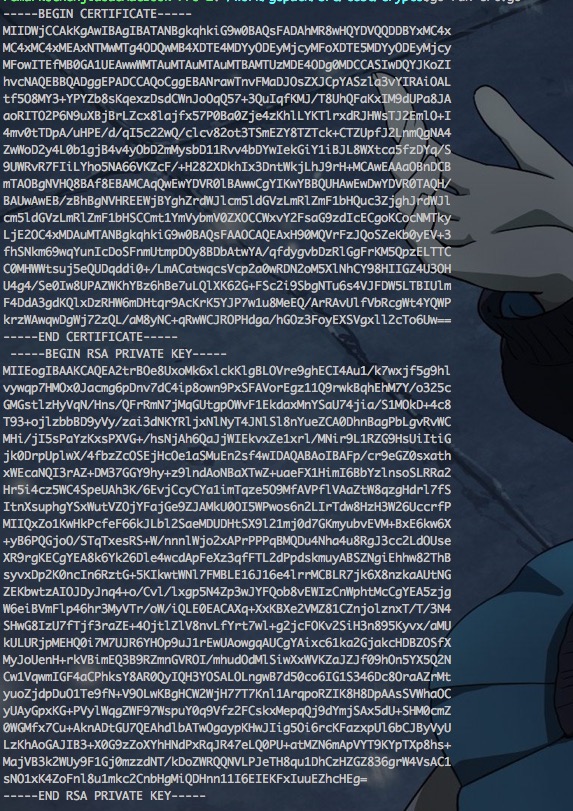
这里我们没有CA,所以我们可以采取使用自己私钥自签名生成证书的方式
这里选用的是k8s的自签名生成证书的方式
1 | package main |
证书与私钥输出如下所示:
综述
经过这篇文章,相信已经对私钥,公钥,证书,签名这些概念有所了解了,在golang中如何调用也应该比较清楚了